Mandiant, a Prominent Cybersecurity Firm, Experienced a Security Breach Due to Insufficient Protection of Its X Account.
Mandiant, a distinguished cybersecurity firm, faced a security breach when its X Account lacked adequate protection. Subsequently, cybercriminals took control, rebranding it as @phantomsolw and leveraging it to promote a deceptive website mimicking the Phantom crypto service.
In this breach, threat actors utilized the compromised account to endorse an airdrop scam, urging followers to verify their eligibility for 250,000 free tokens. The fraudulent scheme aimed to siphon funds from victims' wallets.
The attackers maintained control of the account for an extended period, spanning several hours.
“We are aware of the incident impacting the Mandiant X account. We’ve since regained control over the account and are currently working on restoring it.” reads a statement sent by a Mandiant spokesperson to several media outlets.
The attackers also trolled Mandiant with posts saying. “Sorry, change password please.” and “Check bookmarks when you get account back.” Mandiant launched an investigation into the incident.
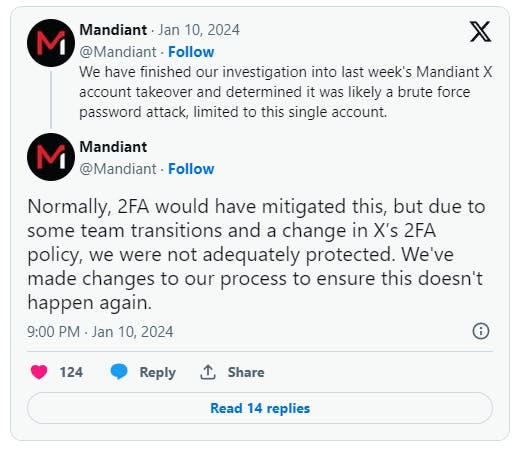
“We have finished our investigation into last week’s Mandiant X account takeover and determined it was likely a brute force password attack, limited to this single account.” the company said on X.
The security firm revealed that it was hacked as a result of a “brute-force password attack,” carried out by a drainer-as-a-service (DaaS) group.
The company admitted that its account was not adequately protected because the 2FA was not enabled.
The attack took place on January 3, 2024, the company’s X account was used to distribute links to a phishing page hosting a cryptocurrency drainer tracked as CLINKSINK.
Multiple threat actors have conducted campaigns since December 2023 that use the CLINKSINK drainer to steal funds and tokens from Solana (SOL) cryptocurrency users. Drainers are malicious scripts and smart contracts that actors use to steal funds and/or digital assets from victims’ cryptocurrency wallets after they are tricked into approving transactions.
“The identified campaigns included at least 35 affiliate IDs that are associated with a common drainer-as-a-service (DaaS), which uses CLINKSINK. The operator(s) of this DaaS provide the drainer scripts to affiliates in exchange for a percentage of the stolen funds, typically around 20%. We estimate the total value of assets stolen by affiliates in these recent campaigns to be at least $900,000 USD.” reads the report published by Mandiant.
The threat actors employed the use of social media and chat applications (i.e. X and Discord) to spread cryptocurrency-themed phishing pages to trick victims into connecting their wallets to claim a bogus token airdrop.
“The observed CLINKSINK phishing domains and pages have leveraged a wide range of fake token airdrop-themed lures masquerading as legitimate cryptocurrency resources, such as Phantom, DappRadar, and BONK (Figures 1-3). These phishing pages have loaded the malicious CLINKSINK JavaScript drainer code to facilitate a connection to victim wallets and the subsequent theft of funds.” continues the analysis. “When a victim visits one of these phishing pages, they are lured into connecting their wallet in order to claim a token airdrop. After connecting their wallet, the victim is then prompted to sign a transaction to the drainer service, which allows it to siphon funds from the victim.”
CLINKSINK drainers are developed to check the current balance on the wallet and steal the crypto assets tricking the victims into signing a fraudulent transaction.
Mandiant discovered numerous DaaS offerings that rely on the CLINKSINK drainer, including ‘Chick Drainer,’ which may now operate at least partially as ‘Rainbow Drainer.'”
The researchers speculate that the source code of the drainers is available to multiple threat actors, allowing them to carry out independent campaigns.
“The wide availability and low cost of many drainers, combined with a relatively high potential for profit, likely makes them attractive operations for many financially motivated actors.” concludes the report that includes YARA Rule for the detection of the CLINKSINK drainer activity “Given the increase in cryptocurrency values and the low barrier to entry for draining operations, we anticipate that financially motivated threat actors of varying levels of sophistication will continue to conduct drainer operations for the foreseeable future.”
Reference: SecurityAffairs

